Scams » Scam And Its Types » Phishing Scam
Phishing Scam
In the field of computer security, phishing is the criminally fraudulent process of attempting to acquire the sensitive information like usernames, passwords and credit card details by masquerading as a trustworthy entity in a communication.
Those messages that direct to your website may look like a legitimate organization's site or to a phone number purporting to be real. But these mails are to be bogus and exist simply to trick you into divulging your personal information so the operators can steal it, fake your identity, and run up bills or commit crimes in your name. To know about detailed analysis on phishing, its types and federal law enforcements and various authoritative sites that battle against phishing scam, several documents and links have been listed here.



























Those messages that direct to your website may look like a legitimate organization's site or to a phone number purporting to be real. But these mails are to be bogus and exist simply to trick you into divulging your personal information so the operators can steal it, fake your identity, and run up bills or commit crimes in your name. To know about detailed analysis on phishing, its types and federal law enforcements and various authoritative sites that battle against phishing scam, several documents and links have been listed here.

Cautions :
Emails or pop-up messages that claim to be from a business or organization you may deal with direct services like Internet service provider (ISP), bank, online payment service, or even a government agency. These messages may ask you to "update," "validate," or "confirm" your account information or face dire consequences and also make it a policy never to respond to emails or pop-ups that ask for your personal or financial information.
Beware of emails which claim that :
Beware of the emails that ask for your personal details like usernames, passwords or credit card details and more. These emails often directs users to enter details at a fake website whose look and feel are almost identical to the legitimate one. Although using a server authentication, it may require tremendous skill to detect that the website is fake.
Interesting Facts about Phishing :
- Spam type email is one of the most common means of phishing.
- It is estimated that 59 million phishing emails are sent every day, of which 1 in 6 are opened.
- Trusteer's study Measuring the Effectiveness of In-the-Wild Phishing Attacks estimates that just one half of one percent of online banking customers are successfully phished, but those incidents still cause $2.4M to $9.4M in annual losses per one million clients.
- According to PhishTank, over 60 percent of the 18,000 phishes reported by members in March 2010 were verified in a medium time of 4.5 hours.
- According to McAfee, 95 percent of phishing e-mails pretend to be from Amazon, eBay, or banks.
- A study by Trusteer estimates that mail-server spam and phishing filters stop 63 percent of phishing e-mails from even reaching in-boxes.
- Phishing is often conducted by organized crime.
List of Phishing types :
Clone Phishing :
Clone Phishing is another smart way to perform phishing scam whereby, a legitimate, and previously delivered, email containing an attachment or link has had its content and recipient address(es) taken and used to create an almost identical or cloned email. The cloned email is then replaced with malicious attachments and sent under a spoofed email address that appears to be original.

Content-Injection Phishing :
Content injection is a type of phishing scam where the hacker injects content or changes a part of the content in order to link or redirect to another page from a reliable website. This phishing scam is done to mislead the target to a page where they are made to enter their personal information that will be hacked by the phisher.

Data Theft :
Data theft is widely used for phishing attacks aimed at stealing confidential information from corporate like important design documents, confidential memos, and company information etc. data theft is usually done with the intention to cause damage to the target or sell the stolen information to competitors. Similar to other types of phishing scams, data theft can occur by means of malicious code running on any computer that can access activation keys to costly software, sensitive information like passwords, account numbers etc.

Deceptive Phishing :
Deceptive phishing is a scam where the phisher sends bulk email messages which influence the user to click on certain link from the email. This is one of the most common types of phishing attack where the user is targeted to reveal his confidential information. Some of the examples of deceptive phishing include, need to verify account information, fictitious account charges, system failure requiring users to re-enter their confidential information, attractive new services requiring immediate action etc.

DNS-Based Phishing ("Pharming") :
In DNS based phishing, phishers tamper with the target's host files and domain name system so that requests for URLs or name service return a bogus address and subsequent communications are directed to a fake site controlled by the hackers. The result: users are unaware that the website where they are entering confidential information is controlled by hackers and is probably not even in the same country as the legitimate website. "Pharming" is the name given to domain name based phishing.

Email / Spam Phishing :
Email/Spam in one of the most common and oldest known type of phishing attack ever. This kind of attack is done by phishers in order to attain sensitive information such as username, passwords, credit card number etc from the user. Scammers used to adopt the means of email in order to send mails that persuaded the user to enter their confidential information. The emails are framed in such a way that the user is forced to believe the bogus email.

Evil Twins :
Evil twin is a term used for Wi-Fi attack which is similar to the nature of spoofing or e-mail phishing. This type of phishing scam is best described as wireless phishing. A phisher fools the user by connecting to a mobile or laptop and appearing as a legitimate provider. Basically, this type of phishing attack is used to steal passwords by snooping the communication link.

Hosts File Poisoning :
Host file poisoning is a type of scam where hackers attack the host file and transmit a bogus address taking the user unwittingly to fake a look a-like website where their credentials are stolen. This is made possible by the phishers because majority of websites are running at Microsoft windows operating system and it first looks up the host name before undertaking the DNS (Domain name server). The aim of phishers in this type of phishing scam is to steal the user's information by poisoning the host files.

Instant Messaging :
Instant Messaging is a type of phishing attack similar to email phishing. Here instead of an email, the user receives an email from the phisher with some information and a link that redirects the user to a phishing website. The information is written in such a way that the user is induced to click the link. The link that follows is designed to look exactly the same as the legitimate website. If the user does not pay heed to the URL, it can be very difficult to differentiate between the original and the fake phishing website. The phisher then collects the user's information on the fake phishing website page.


Key-loggers and Screen-loggers :
Screen Loggers and Key Loggers are particular varieties of malwares that track the keyboard input by the user and send the information to the phisher via internet. These malwares embed into the users browsers in the form of a small utility program that run automatically once the browser is started. Such malwares are known as helper objects that can also run into system files as device drivers or screen monitors. The below screenshot is an example of a real time phishing scam done through key logging:

Link Manipulation :
Link Manipulation is a technique in which the phisher sends or adds a link to a well known and popular website. If the user happens to click on the deceptive link, the user id redirected to the phishing page. Phishers are also adding backlinks to popular pages that are then redirected to their bogus pages that look like legitimate pages. It is very difficult for the user to identify from the URL as phishers redirect the URL after it has been clicked.

Malware Phishing :
Malware phishing is a technique which aims at making the malware files to be run on the user's computer. These malware files are either sent as an attachment, or a downloadable file that will start functioning as soon as it is clicked. Malware programs are designed by phishers that can cause damage to the user's data and can also send sensitive information from the user's computer to the phisher via email.

Malware-Based Phishing :
Malware based phishing is a phishing scam where the phisher manages to run malicious software on the user's (target) PC. This malware is programmed to detect the confidential information that is stored on the user's PC or track information entered by the user. Such malware's are introduced into the target system by means of an email attachment, a downloadable file from the web or by exploiting known security vulnerabilities.

Man-in-the-Middle Phishing :
Man in the middle phishing is the type of phishing which is the most difficult to detect, as in this form of phishing scam the phisher position themselves between the user and the original website or the system. They record the information entered by the user and continue to pass the user to the regular transactions so that there is no suspicion. After the process in over, the phisher uses or sells the recorded information.

Mass Phishing :
Mass phishing attack is aimed at a huge target audience who may or may not be related to the service mail that is sent. The intention of the phisher is to attack as many users as possible. The scammer does not bother about who opens the mail and who does not. This kind of phishing attack is done to cover a vast amount of audience and then the probability of success is determined later. Mass phishing is similar to throwing fishing net with the intention to catch as many number of target fishes as possible.

Phone Phishing :
Phone phishing is yet another type of phishing scam where the phisher makes phone calls to users and makes them dial numbers which ask for verification of user information. The user when dials or presses the account or credit card information for verification purpose, the phisher grabs the required information in order to make fraud transactions. It is basically carried out through fake caller IDs. Phone phishing is less popular these days due to the security systems being tightened.

Search Engine Phishing :
Search engine phishing is a type of phishing scam where phishers create attractive websites alluring the customers to enter their personal information. These websites manage to get legitimately indexed in search engines and users end up to such websites in the normal course of their search. An example of search engine phishing can be a website created as a banking website giving extra benefits than any normal bank offers. Customers are lured to enter their data and end up getting deceived.

Session Hijacking :
With the popularity of e-commerce websites and online banking transactions, there is a sudden rise in a type of phishing scam known as "Session Hijacking". In this type of phishing scam, the activities of users are monitored until they log into a vulnerable area (such as checkout in shopping websites or a banking site) where the user enters the credentials. At such occasions, the malicious software takes control and takes unauthorized actions such as transferring funds or hacking the credit card details without the knowledge of the user.

Spear Phishing :
Spear Phishing is by far the most successful on the internet today, as phishers in this type of phishing scam gather all the necessary information about the target. This phishing attack is usually directed towards specific individuals or companies. A spear phisher gathers information about the target in order to increase the probability of success of the attack. Spear phishing attacks are not initiated by "random hackers" but are more likely to be initiated by perpetrators.

Spy phishing :
Spy phishing is one among the latest phishing scams that borrows its techniques from phishing and spyware. The term "spy phishing" was coined by Jeffery abound in 2006. Through the use of spyware, spy phishing aims at stealing the user information by means of prolonged phishing attacks. Prolonged phishing attacks are those where the spyware doesn't cause any attack to the user's system until the user enters vulnerable areas.

System Reconfiguration Phishing :
System Reconfiguration as the name suggests, is a type of phishing attack where the system settings of the target's PC are modified for malicious purposes. A very common example of system reconfiguration attack can be, altering the URLs and directing them towards similar looking or sounding URLs that intend to hook the user in phishing attack. For example, the URL of the user's bank that is frequently used may be stored on the "favorites" section or may be changed to a similar looking URL which the user might not pay much heed to.

Tabnabbing :
Tabnabbing is one of the recent phishing scams discovered in the early 2010 by Aza Raskin. Tabnabbing, unlike other phishing scams, works in a reverse order. Instead of influencing the user to click on a link to obtain the user credentials, the phisher loads a fake page in one of the open tabs in the user's browser. Hence the name is given as Tabnabbing.

Web based delivery :
Web based delivering phishing is one of the most sophisticated phishing technique ever know. It is very similar to the "man in the middle" phishing technique where the phisher is located between the original website and the targeted user. In this type of phishing scam the usual process of the user is not interrupted, where by making the user believe that nothing is going wrong. As the user continues to enter the sensitive information, the phisher in the middle collects all the necessary information thus making the phishing attack successful without the knowledge of the user.

Web Trojans :
Web Trojans are a type of phishing scam where the phishing process is designed in the form of pop up that appears invisibly when users are trying to log into any vulnerable area. These pop ups collect the information entered by the user and transmit it to the phisher via internet. Web Trojans are basically designed to collect user's credentials through a local machine. The below screenshot is an example of web Trojan pop up, where the fields highlighted in red are additional fields injected in order to acquire user's personal information. Once these data is entered by the target, it is transferred to the command and control host.

Whaling :
Whaling is a term given to a phishing attack where senior executives and other high profile person's are targeted. In the recent past, it is observed that most of the phishing attacks are targeted to senior high profile people in the business industry. The content of a whaling attack email contains legal documents and executive issues. Whaling phishers tend to forge the official looking emails and documents and insist the user to click on an intended link to spread malware.
In the below screenshot, the user is directed towards clicking the link, which will lead to download of masquerading software that will access user's private information.

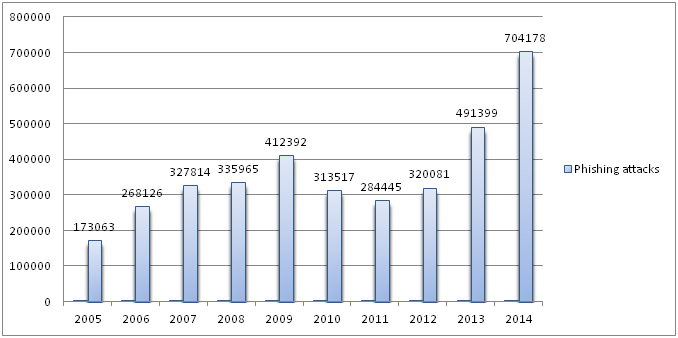
STATISTICS :
The below chart displays the number of phishing attacks incurred from the year 2005 to 2014.
Data Source: Wikipedia
Data Source: Wikipedia

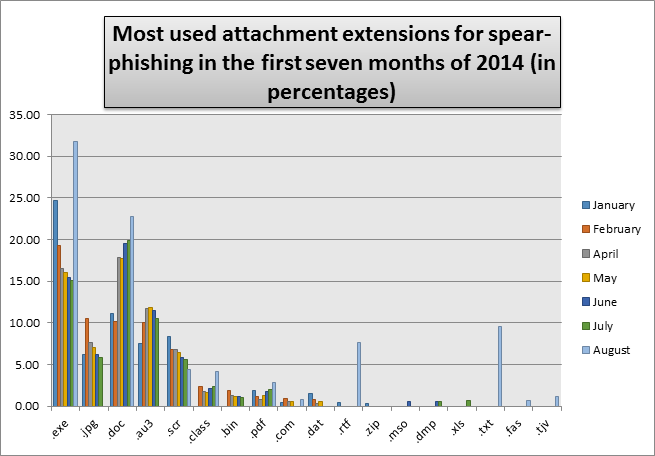
Below mentioned is an analysis of spear phishing file attachment extensions which are most commonly used.

Feel Free to use our Spam Checker Tool :
We are providing the Spam
Checker Tool for your convenience. Here you can enter the email or the contact number that you suspect to be a scam. This tool checks it with our spam database list and ensure you regarding the email or the phone number is real one or bogus.
Report scam to United States government-you could file a complaint about scam or other crime here.
Report scam to United States government-you could file a complaint about scam or other crime here.
